Unlocking IT Quality: Your Regional Managed Provider
Unlocking IT Quality: Your Regional Managed Provider
Blog Article
Strategize and Range WITh Proven IT Managed Solutions Approaches
In the fast-paced landscape of contemporary company, the critical use of IT took care of solutions has come to be a cornerstone for companies intending to enhance operational performance and drive sustainable development. By carrying out proven methods customized to meet certain business requirements, companies can navigate the intricacies of innovation while continuing to be agile and competitive in their respective markets.
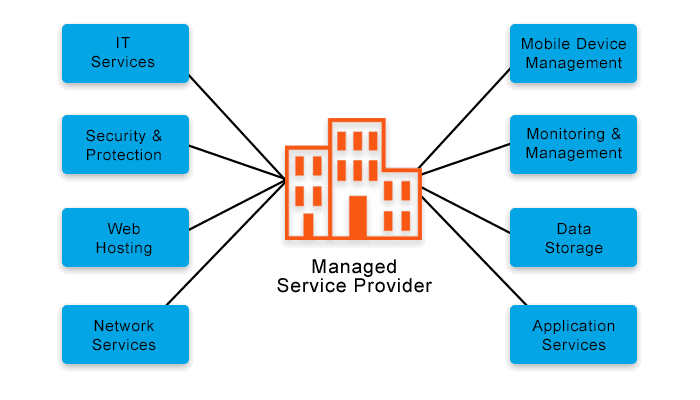
Advantages of IT Handled Services
By outsourcing IT administration to a specialized company, companies can touch into a wide range of competence and sources that would otherwise be expensive to maintain internal. One of the essential benefits of IT Managed Services is positive tracking and upkeep of systems, which aids stop possible concerns before they intensify right into major issues.
Moreover, IT Managed Provider can give access to the most up to date innovations and finest techniques without the need for constant investment in training and facilities upgrades. This makes sure that businesses remain affordable in a rapidly advancing technological landscape. Furthermore, by unloading routine IT jobs to a taken care of services service provider, inner IT teams can focus on strategic campaigns that drive development and development for the company. In final thought, the advantages of IT Managed Providers are instrumental in enhancing procedures, improving effectiveness, and ultimately, driving business success.
Secret Approaches for Implementation
With an understanding of the substantial benefits that IT Managed Services deal, organizations can now focus on applying key approaches to successfully incorporate these services into their procedures - managed service provider. In addition, companies have to establish clear communication channels with their taken care of service provider to make certain smooth collaboration and timely concern resolution.
Another essential method is to prioritize cybersecurity steps. Data violations and cyber risks position considerable dangers to services, making security a leading priority. Executing durable security protocols, regular surveillance, and timely updates are vital action in guarding delicate details and keeping company continuity.
Furthermore, companies ought to develop solution level contracts (SLAs) with their taken care of provider to define assumptions, responsibilities, and efficiency metrics. SLAs assist in establishing clear standards, ensuring responsibility, and maintaining solution quality requirements. By including these key strategies, services can leverage IT Took care of Provider to streamline operations, boost effectiveness, and drive sustainable growth.
Making Best Use Of Effectiveness Through Automation
Moreover, automation makes it possible for real-time surveillance and information analysis, supplying useful understandings for informed decision-making. By automating routine surveillance tasks, businesses can proactively deal with issues prior to they intensify, decreasing downtime and enhancing efficiency (managed service providers). Furthermore, automation can promote the seamless assimilation of various systems and applications, enhancing partnership and information circulation throughout the organization
Ensuring Information Protection and Conformity
Data safety and compliance are extremely important worries for services running in the digital landscape these days. With the increasing quantity of sensitive data being saved and processed, making certain durable safety and security actions is critical to secure against cyber risks and comply with regulative requirements. Executing extensive data security methods entails securing data, developing access controls, on a regular basis upgrading software program, and performing protection audits. Moreover, abiding by regulations such as GDPR, HIPAA, or PCI DSS is necessary to keep and avoid expensive charges trust fund with consumers. Managed IT providers play a crucial role in aiding companies browse the complex landscape of information safety and security and compliance. They offer expertise in implementing safety and security protocols, checking systems for prospective breaches, and making sure adherence to sector guidelines. By partnering with a reliable managed providers, services can improve you could check here their data safety and security position, mitigate risks, and show a commitment to securing the discretion and honesty of their data possessions.
Scaling IT Facilities for Growth
Including scalable IT framework solutions is crucial for promoting organization growth and functional performance. As business expand, their IT needs advance, requiring infrastructure that can adjust to enhanced demands effortlessly. By scaling IT facilities successfully, companies can ensure that their systems continue to be trustworthy, secure, and performant even as work grow.
One key facet of scaling IT framework for growth is the capability to flexibly allot resources based on present demands. Cloud computer services, for example, offer scalability by allowing companies to change storage, refining power, and other sources as needed. This elasticity enables business to effectively manage spikes in need without over-provisioning resources during durations of reduced task.
Moreover, carrying view it out virtualization technologies can improve scalability by making it possible for the production of digital instances that can be quickly duplicated or modified to suit altering work - it managed service providers. By virtualizing web servers, storage, and networks, companies can optimize source utilization and enhance IT monitoring procedures, inevitably sustaining company growth initiatives effectively
Final Thought
Finally, applying IT took care of services can bring countless advantages to a company, such as boosted performance, enhanced information security, and scalability for growth. By that site following key techniques for application, making use of automation to make the most of performance, and guaranteeing information security and compliance, businesses can much better plan and scale their IT framework. It is critical for companies to adapt and progress with technological developments to remain affordable in today's ever-changing landscape.
Report this page